Bad emails / Malware emails / Scam email
Emails fly about between servers and computers all day, thousands every second around the world are sent. Most of the emails are legitimate. But the email system is open to abuse. There are holes in it.
I categorise bad emails in 2 sections, those with attachments and those who try and get you to download attachments. The 2 examples below are the latter.
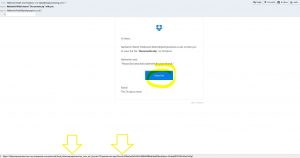
How do you know a legitimate email?
Above is an image of what I call a bad email. It’s an email that looks perfectly good, from Dropbox, it even has a no reply email from dropbox. But clicking on the “view file” link will take you off to a website that is unknown. It might be a site that looks like Dropbox, but even by clicking that link the sender of the email will know they have a live email address. This could be the start of a series of targeted emails to gain personal information / money / trust etc.
So how do you tell this is a bad email?
First, think who is this person, Nathaniel Walsh? If you know him, great, but DO NOT assume the file is safe.
Are you expecting an email from him with a statement? If you’re not, give him a call and ask him, it takes 2 minutes! If he has not sent you an email then it could be a scam, his computer or email system could have been breached and you and other people from his address book might have been targets by scammers/hackers.
Also check the links in emails, don’t click on them! But hover your mouse over the link and see where it will take you. If it is a place that isn’t that of the email that has been sent, then it is likely a fraudulent email.
Another example
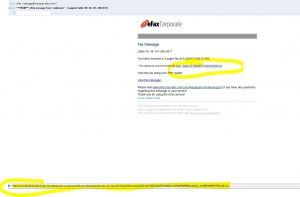
Take a look at this image of an email. You think someone has tried to use 20th century technology in a 21st Century way. You might wonder what it is. But first, do you recognise the caller ID? It is 0151, a quick google shows it is from Liverpool. Are you expecting anything from a company in Liverpool? Do you do business with a company in Liverpool? If you look at what is sent via fax, really only legal documents are faxed these days. There will be the odd occasion when faxes are used, but it is rare and it has been felled by email and pdf documents.
You will also notice the domain the link sends you to is about truck hire Australia, have you hired a truck in Australia from a company in Liverpool?! This is obvious that it is spam or a scam as those 2 situations for myself are untrue.
Again, if you have hired a truck in Australia from a company in Liverpool, give them a call and ask, “have you sent me an efax message?” If they say no, it’s a scam! Maybe it is a coincidence or maybe it’s a specific attack.
If you suspect it is a specific attack attempt then you engage with our security consultation service and we can advise. Contact sales@thecomputersaint.com to consult with us.
If you find yourself with an email and an attachment from either a known person or unknown person then follow the rule of call that person up. Ask them if they’ve sent you an email with an attachment. If they haven’t tell them you have received something from them, they should investigate this and you might need to send the email to their IT team. It’s unlikely to do any damage sitting in your inbox. If you click links or download the file then that is when the damage is done.
Even with files that attached and from a trusted source, that you are expecting you should download the file to a directory (or folder) on your computer and then with modern antivirus software you can run a scan on the file and tell if it is safe. Don’t run the file, even if it is a .docx (document) file or something you’ve trusted in the past.
Emails with attachments
Emails often come to us with an attachment; most modern antivirus software will allow us to scan as the attachment is downloaded. This method is good if you’re using a laptop to download an email. I’ve sometimes been emailed by family members, colleagues or customers who have had some malware infect their computer, only to find I get an email from them with a strange attachment that I was not expecting.
If you have an email like this, the advice is the same as above: call the person and ask them if they’ve actually sent you an email as they might not know they have a problem. If they have then it should be OK, but you should download the email and scan it first with Antivirus anyway!
To summarise:
Identify emails.
Call the person you’ve got the email from.
If you get a bad email:
Don’t click the links, see where the link goes.
Tell the company in question, some of the larger companies especially have teams of people (IT team normally) who deal with SPAM & Bad emails. The company might ask for the email to be forwarded to them.
Scan any downloads with a virus program. I like Avast or AVG (free versions are good)


